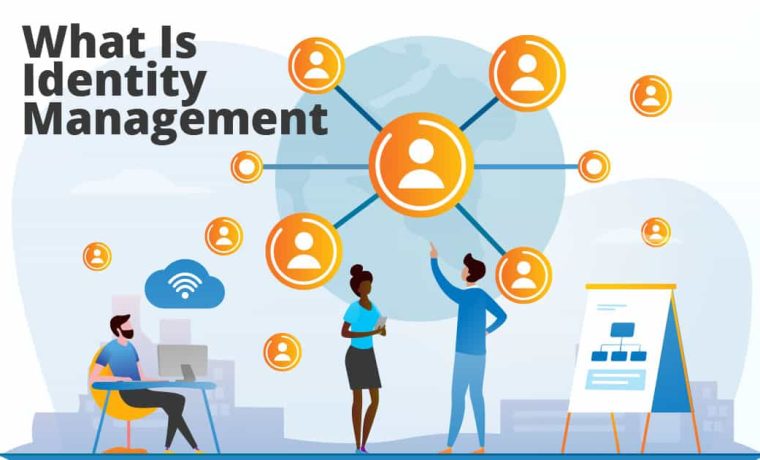
Individuals, businesses, and organizations of all sizes are turning to Identity and Access Management (IAM) software to ensure the security of their digital resources and to maintain access control. As IAM solutions become more advanced, it is essential for organizations to understand the features of contemporary IAM software and how to use them to their greatest advantage.
We will explore the various features and capabilities of IAM software and how to use them to master identity management. We will also discuss best practices for implementing IAM software in an organization and how to ensure that the system is secure and up-to-date. By the end of the post, readers should have a better understanding of how to utilize IAM software to its fullest potential and to reduce the risk of unauthorized access.
- Use IAM to secure sensitive data.
The Tools4ever software suite helps organizations to leverage IAM capabilities to prevent unauthorized access to sensitive data. With the IAM software tools, organizations can define the access rights for different groups of users and apply them across the organization. Additionally, the software allows for the implementation of multi-factor authentication and user activity tracking to ensure that only the right users are accessing sensitive data. This helps organizations to protect their data from unauthorized access and maintain regulatory compliance.
- Use authentication, authorisation, and auditing to comply with industry regulations.
Mastering identity management with Tools4ever software features includes leveraging IAM components such as authentication, authorization and auditing to ensure compliance with industry regulations. Authentication verifies the identity of users, while authorization allows organizations to control access to resources. Auditing provides a record of who is accessing what resources and when, enabling organizations to track and address potential security risks.
- Create granular access control rules to ensure secure access to systems and data.
Mastering identity management with IAM software features from Tools4ever helps organizations control access to systems and data. By creating granular access control rules, organizations can set up secure permission levels for users and groups. This ensures only authorized personnel can access or modify protected information. Tools4ever also provides tools to easily manage access control in the cloud, on-premises, or in hybrid cloud environments. With these features, organizations can protect valuable data and maintain compliance with the latest industry standards.
Conclusion.
IAM software provides the tools to ensure organizations can effectively manage user access and security. With the right implementation and regular monitoring, IAM software can provide a more secure and efficient approach to identity management. By leveraging the features offered by IAM software, organizations can not only increase their security, but also gain improved control over their digital identity and access management.